Onboard a Linux device to a network with certificates and Certmonger
In this topic, you will learn how to onboard using certificates, the Certmonger service, a Linux computer, and a network managed by Portnox™ Cloud.
Disclaimer: PortSCepX is provided as a convenience tool developed by the Portnox team for use by selected customers. It is not an officially supported product, and Portnox makes no guarantees, representations, or warranties – express or implied – regarding its performance, reliability, suitability, or fitness for any particular purpose. Use of the script is at your sole risk. Portnox assumes no responsibility or liability for any issues, damages, or losses arising from its use, modification, or execution in customer environments. Instructions for use are included within the script.
If you already downloaded and installed the certificate for the same device, for example, to authenticate with another type of network, you don’t need to install the certificate again and you should skip the relevant steps.
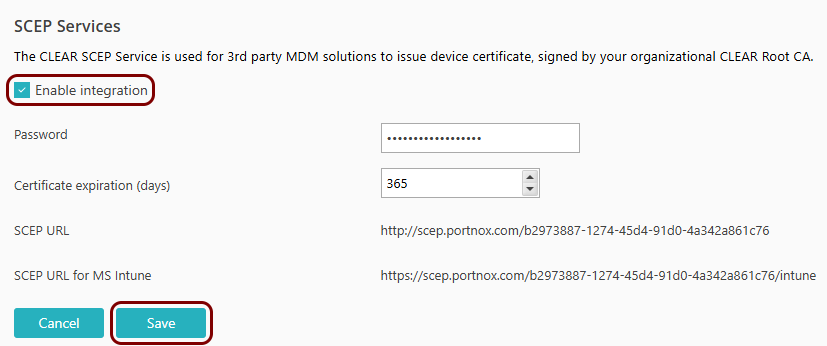
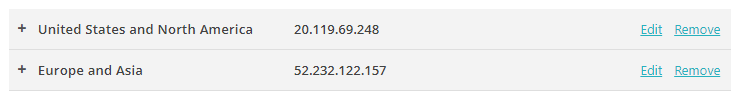
Turn on the Portnox Cloud SCEP services
In this section, you will configure Portnox™ Cloud to provide SCEP services to your devices.
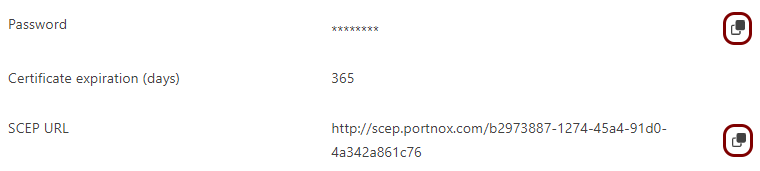
If you have previously turned on the Portnox Cloud SCEP services, skip to the step in which you get the Cloud SCEP URL and secret.
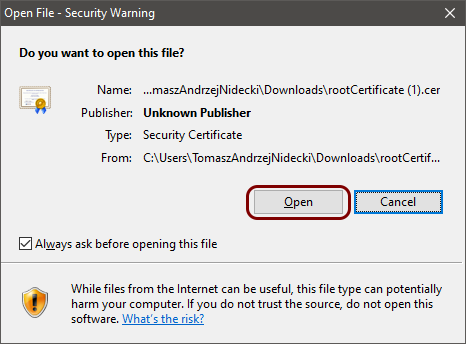
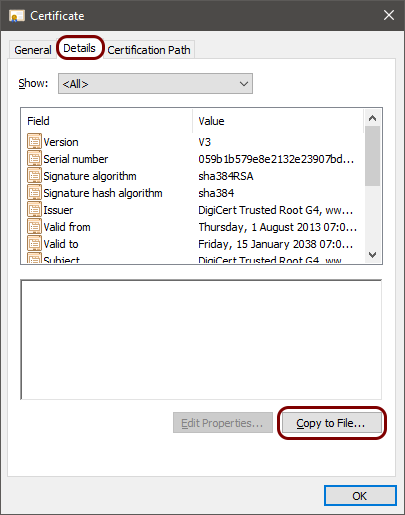
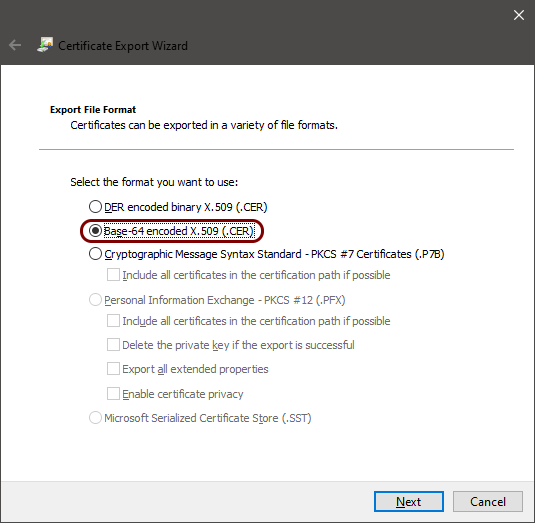
Download and convert the root CA certificate
In this section, you will download the Portnox™ Cloud root CA certificate> from the Cloud portal and convert it to a format that you can later use to connect to the network.
Request the device certificate using Certmonger
In this section, you will use the Certmonger software available on all Linux distributions to request a certificate for your device using the SCEP protocol and Portnox™ Cloud SCEP services.
Result: You have obtained a private/public key pair for your device, which you can now use to configure your connections to your networks managed by Portnox Cloud.
Troubleshooting: use $sudo getcert list to list your Certmonger request and see any reasons for potential problems.
Configure your network connection with the Portnox Cloud certificate
In this section, you will configure NetworkManager on Linux to connect to the network managed by Portnox™ Cloud using your user certificate and private key.