Configure ZTNA with on-premises resources and a Linux Docker container
In this topic, you will learn how to configure the Portnox™ ZTNA remote private access method to allow your remote users to access your private resources hosted on-premises, by using a Docker container in an on-premises machine with Linux.
In this scenario:
-
You want your remote users to be able to access private resources that you host on-premises.
-
You need to host a Portnox Docker container in the on-premises local network to be able to access these resources. You want to use a Linux-based physical or virtual machine to run Docker and host the container.
We assume that you have already set up a physical or virtual machine on your chosen platform with Linux installed. We also assume that this machine is running in a network that has direct access to the resource. We will provide examples for Ubuntu and Red Hat, which you can easily adapt for other Linux distributions.
We also assume that you already distributed certificates to your client devices.
Set up the ZTNA gateway in Portnox Cloud
In this section, you will set up a ZTNA remote private access gateway in Portnox Cloud, install Docker on your machine, and run the Portnox ZTNA remote private access Docker container.
- Optional:
On your Linux-based machine, install Docker using your distribution’s package management framework.
Important: If Docker is already installed, skip this step. If you don’t have a physical or virtual machine to install Docker, you can get a third-party Linux image. For example, you can download the latest Ubuntu image from the Linux VM Images project and import it into your hypervisor.
Ubuntu:
sudo apt-get install docker.io -yRedHat:
sudo yum install -y yum-utils$sudo yum-config-manager --add-repo https://download.docker.com/linux/rhel/docker-ce.repo$sudo yum install docker-ce$sudo systemctl start docker -
In the top menu of Portnox Cloud,
select the option. Then, on the Gateways screen, click on the + Create
gateway button.
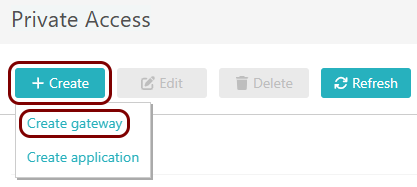
-
On the Create gateway screen, enter a name for this gateway in the
Gateway friendly name field, and in the Region field, select
either EUS Node 1, EUS Node 2, or WEU Node 1.
Then, click on the Create gateway and generate Docker commands button.
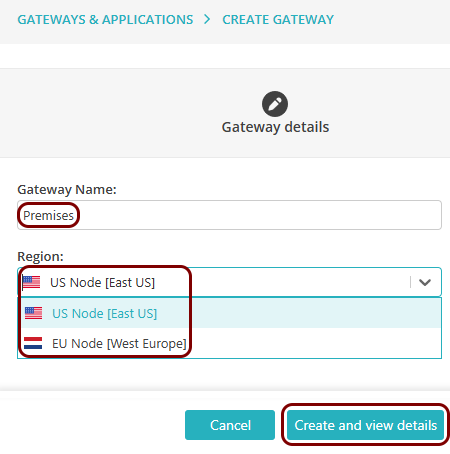
-
In the Provision container step, click on the Copy
command link under the displayed Docker command to copy the command to the clipboard.
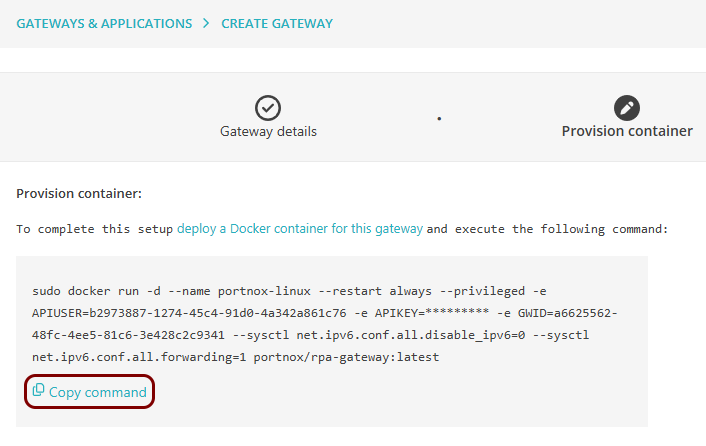
- Paste the copied command in your machine’s terminal window to run the Docker container.
Set up the ZTNA remote private access resource in Portnox Cloud
In this section, you will set up a ZTNA remote private access resource in Portnox Cloud and configure it to access your private resource hosted in the same local network as the Docker container.
-
In the top menu of Portnox Cloud, select the option. Then, on the Resources screen, click on the + Create
resource button.
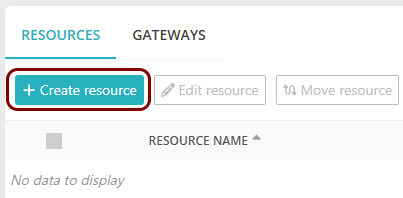
-
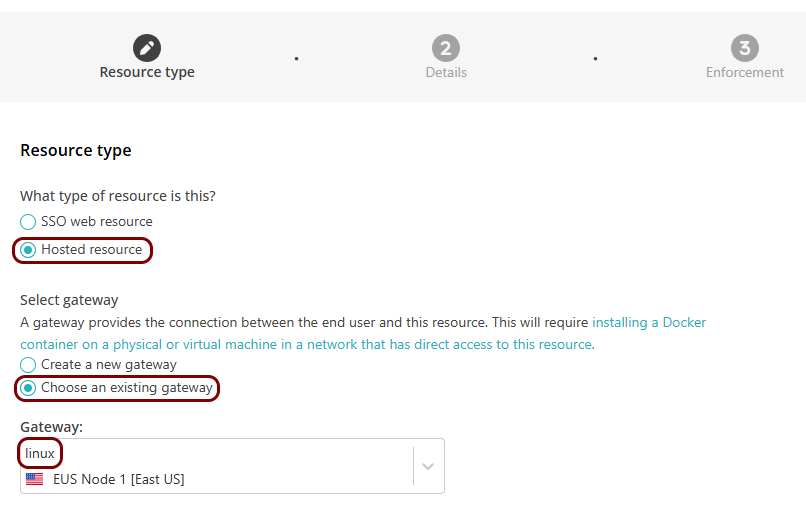
In the Resource type step, select the Hosted
resource option, and then the Choose an existing gateway option. In the
Gateway field, select the gateway that you have just created. Then, click on the
Next button.
-
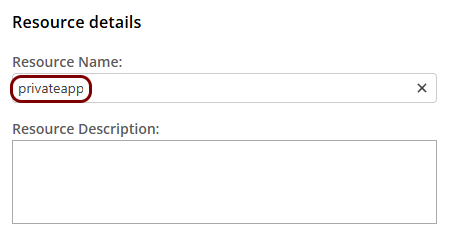
In the Details step, in the Resource Name field, enter the
name for this resource and optionally the Resource Description.
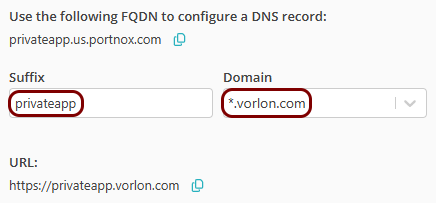
Note: The Resource Name must be a valid subdomain name, because the URL will be constructed using this name. You should only use lowercase letters, digits, and hyphens.
Result: If you want to use the Portnox URL, you can copy the URL for your resource by clicking on the ⧉ icon.
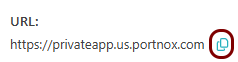 Note: Make sure to check if your web resource will accept connections when accessed using this URL. If your web security solution has an anti-CSRF feature, you will need to configure it to allow this URL.
Note: Make sure to check if your web resource will accept connections when accessed using this URL. If your web security solution has an anti-CSRF feature, you will need to configure it to allow this URL. - Optional:
If your resource uses the same IP address and port as other resources:
Note: This is quite a common situation, for example, when you use a single on-premises web server to host several resources, and you create internal domain names for these resources such as: confluence.vorlon-onpremises.com or jira.vorlon-onpremises.com.
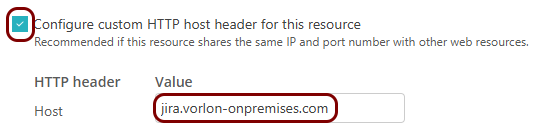
- Activate the Configure custom HTTP host header for this resource checkbox.
- In the Value column, enter the host header value.
- Optional:
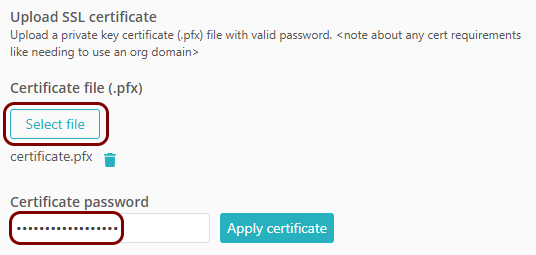
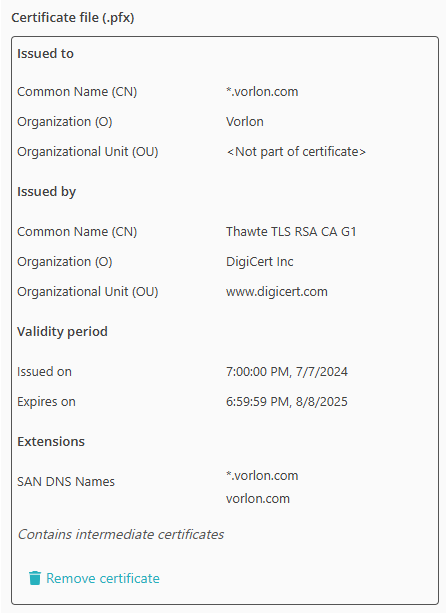
If you want to use a URL in your own domain for the resource:
-
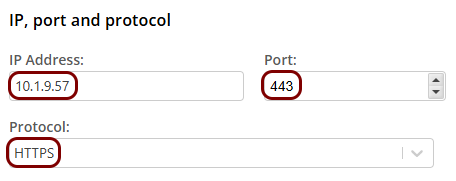
In the IP, port and protocol section, enter the details of the hosted resource in the
IP Address, Port, and Protocol
fields.
- Click on the Next button.
- Optional: In the Enforcement step, change the setting to Override with custom policy and then select a risk assessment policy if you want to control access to this resource using a custom risk assessment policy.
- Click on the Add resource button to save your configuration.
Result: Your users can now access your private resource by typing the URL in their browser.
Automatically update an existing local server container
In this section, you will learn how to automatically update your Docker container to the latest version by deploying another Docker container: portnox-autoupdate.
-
Note down the organization ID:
-
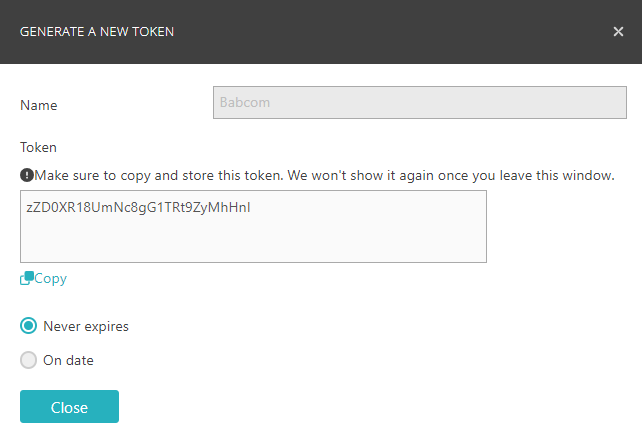
Get an API token from Portnox Cloud:
-
Deploy the portnox-autoupdate Docker container:
sudo docker run --restart=always -d --name portnox-autoupdate \ -v /var/run/docker.sock:/var/run/docker.sock \ -v portnox-autoupdate-logs:/app/logs \ -e AUTO_UPDATE_ORG_ID=your_organization_ID \ -e AUTO_UPDATE_PORTNOX_API_TOKEN=your_API_access_token \ portnox/portnox-autoupdate:latestFor example:
sudo docker run --restart=always -d --name portnox-autoupdate \ -v /var/run/docker.sock:/var/run/docker.sock \ -v portnox-autoupdate-logs:/app/logs \ -e AUTO_UPDATE_ORG_ID=b2973887-1274-45c4-91d0-4a342a861c76 \ -e AUTO_UPDATE_PORTNOX_API_TOKEN=zZD0XR18UmNc8gG1TRt9ZyMhHnl \ portnox/portnox-autoupdate:latest