Configure advanced RADIUS server options
In this topic, you will learn how to configure advanced options for Cloud RADIUS servers in Portnox™ Cloud.
Before you begin, you must have an active Cloud RADIUS server in Portnox Cloud. To create a Cloud RADIUS server, read the following topic: Create Cloud RADIUS servers.
Settings described in this topic are optional and allow you to have more control over your RADIUS servers.
-
In the Cloud portal top menu, click on the Settings option.
-
In the Cloud portal left-hand side menu, click on the Services > CLOUD RADIUS SERVICE > Cloud RADIUS instance option.
The right-hand pane shows the list of active servers.
-
Edit the security options for active RADIUS servers.
- Click on the selected RADIUS server to show its configuration.
-
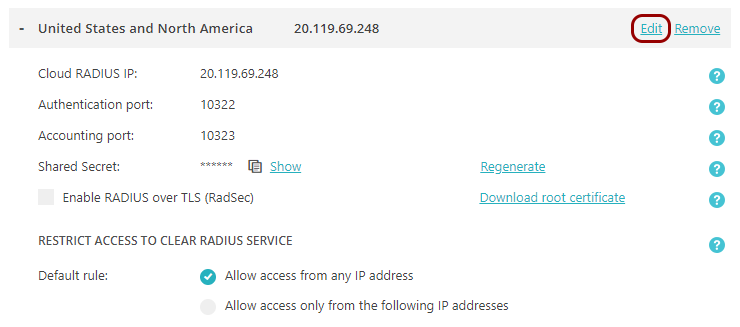
Click on the ⋮ > Edit menu option on the right-hand side.
-
Click on the Enable RADIUS over TLS (RadSec) checkbox to activate it if you want to
allow your NAS devices to communicate with the selected RADIUS server using RadSec.

-
If your NAS devices support mTLS (mutual TLS) for RadSec, click on the Validate NAS Client
Certificate (RadSec) checkbox to activate it.
 Important:for mTLS to work, you must download a trusted root certificate from your NAS device platform, and then upload this trusted root certificate in the Settings > Services > GENERAL SETTINGS > Trusted Root Certificates section by clicking on the Upload trusted root certificate generated by... link.
Important:for mTLS to work, you must download a trusted root certificate from your NAS device platform, and then upload this trusted root certificate in the Settings > Services > GENERAL SETTINGS > Trusted Root Certificates section by clicking on the Upload trusted root certificate generated by... link. -
If your wireless devices support the 802.11r protocol, activate the Enable EAP session
resumption checkbox. Then, if needed, change the default Session lifetime
(hours) value.

If this setting is on, and your wireless device supports the 802.11r protocol, then if that device loses connection to the local RADIUS server and reconnects within the session lifetime, it can authenticate quickly by providing a valid connection session ID.
Note:The session lifetime counts from the last successful connection, not the disconnection. -
If you enabled RADIUS over TLS, click on the Download root certificate link on the
right-hand side to download the root certificate file.
You must copy this root certificate to NAS devices that support RadSec so they can communicate with the RADIUS server.
-
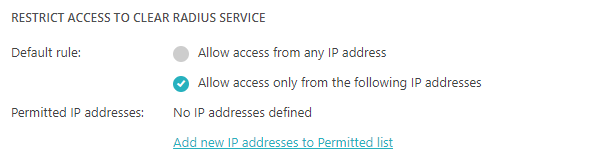
In the RESTRICT ACCESS TO Cloud RADIUS SERVICE section, you can change the setting from
the default Allow all IP addresses to one of the other options:
-
Allow only the listed IP addresses: Only NAS devices with public IP addresses or ranges that are listed will be able to communicate with this RADIUS server.
-
Allow all except the listed IP addresses: NAS devices with public IP addresses or ranges that are listed will be denied access to this RADIUS server.
-
-
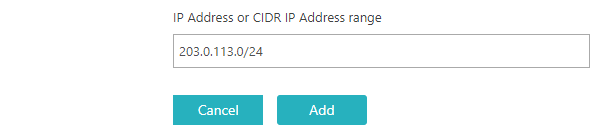
If you selected the Allow only the listed IP addresses option or the Allow
all except the listed IP addresses option, click on the See and edit IP
addresses link and in the IP address allow/block list window, enter the IP
address or the IP address range in the CIDR format, and click on the
Add IP Address button. If you want to remove a selected IP address or range, click on
the checkbox next to the row representing the IP address or range to select it, and then click on the
Delete button. When finished, click on the Update IP List
button.
-
Click on the Save button to save your changes or click on the
Cancel button to abandon all changes.

After you click on one of the buttons, Portnox Cloud will exit the edit mode.
-
Manage the RADIUS anti-flood protection.
-
If you suspect your devices are blocked due to excessive activity, click on the Blocked devices for
excessive activity link.
Your browser will open the BLOCKED DEVICES FOR EXCESSIVE ACTIVITY screen.
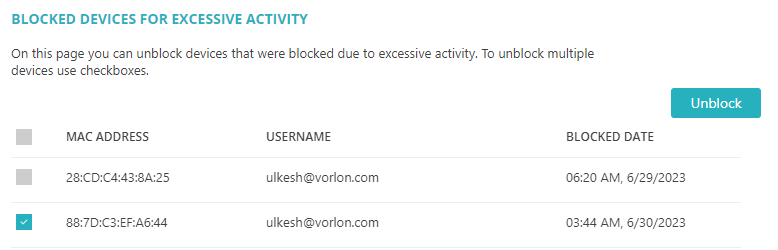
- Select checkboxes next to blocked devices and click on the Unblock button to unblock.
-
When finished, click on the Back button in the top-right corner.
-
If you suspect your devices are blocked due to excessive activity, click on the Blocked devices for
excessive activity link.
-
Configure RADIUS forwarding rules.
RADIUS forwarding rules let you redirect selected RADIUS requests to other RADIUS servers.
To configure RADIUS forwarding rules, read the following topic: Configure RADIUS forwarding rules.
-
Modify the advanced configuration.
At the moment, the Advanced configuration section only has one option.
-
Click on the Advanced configuration heading.
Your browser will show advanced configuration options under the Advanced configuration heading.
- Click on the Edit link to edit advanced configuration options.
-
Select the Use Radius request's public IP for NAS detection during VPN authentication
checkbox to activate this option.
If you turn this option on, the Cloud RADIUS server will use the public IP address from the incoming RADIUS request to identify the NAS from which the VPN authentication is being initiated. This can be useful in scenarios where the NAS is located behind a NAT device or a load balancer.
-
Click on the Advanced configuration heading.
