What are accounts, groups, policies, and sites?
In this topic, you will learn what we mean by accounts, groups, policies, and sites in Portnox™ Cloud.
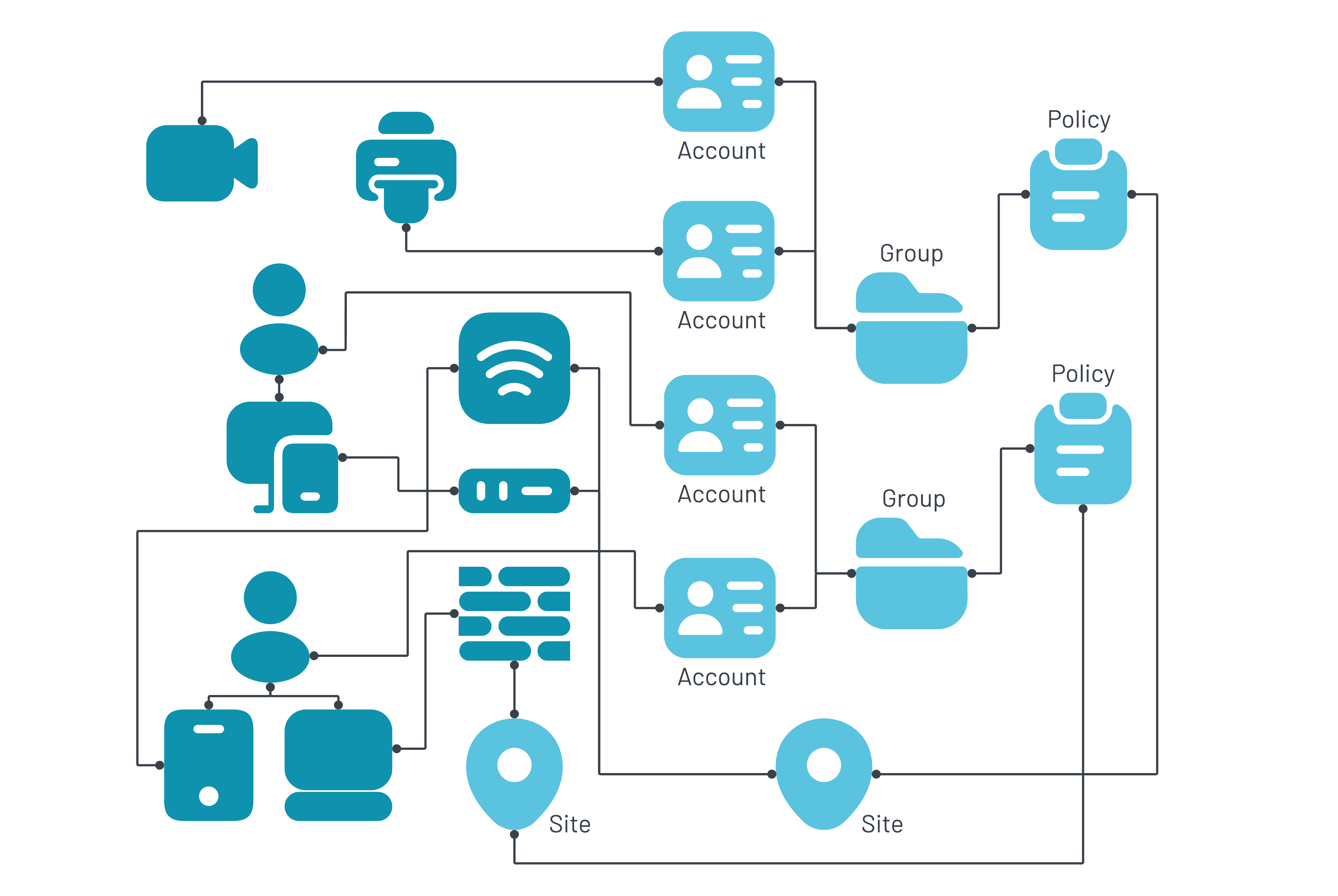
What are accounts in Portnox Cloud?
An account in Portnox Cloud represents a person or device that needs access to the network.
-
For devices that are used directly by people, such as computers or mobile phones, it makes sense to control network access for the person, not the device. In such case, you can create an account for the person, and the person can use the account credentials to log in using different devices.
-
For devices that run automatically, such as printers, scanners, IP cameras, and other IoT devices, it makes sense to control network access for the device, not any particular person. In such case, you can create an account for the device.
Note:You can create an account for a group of similar devices, for example, a group of printers, but individual device accounts are recommended for more granular control.
Account types
-
Portnox account
If you don’t use any authentication repositories such as Entra ID, Google Workspace, Okta, Active Directory, or OpenLDAP, you can use Portnox Cloud to keep a list of your users and groups, and manage them. In such cases, you create Portnox accounts for each user, based on their corporate email address.
-
LDAP account
If you use an external authentication repository, you can create an account in Portnox Cloud that is linked to the LDAP user from that repository.
-
Contractor account
If you need to let contractors access your network, and you cannot create Portnox accounts for them because they don’t have a corporate email address, you can create a contractor account based on any email address and a password.
-
MAC-based account
If you have devices that do not support 802.1X authentication and cannot provide any user credentials to the cloud RADIUS server, you can create accounts for such devices linked to their MAC addresses. The MAC address is treated as the identifier that such devices use to access the network.
Note:We recommend that you do not create MAC-based accounts for devices that support the 802.1X protocol, and that are used by people, because it lets anyone with access to such a device access the company network. -
Device-type account
If you do not want to create individual MAC-based accounts because there are a lot of unmanned devices that need access to your network, you can create a device-type account. For example, you can create an account for all devices of a specific type, from a specific manufacturer, with a model name that contains a specific string.
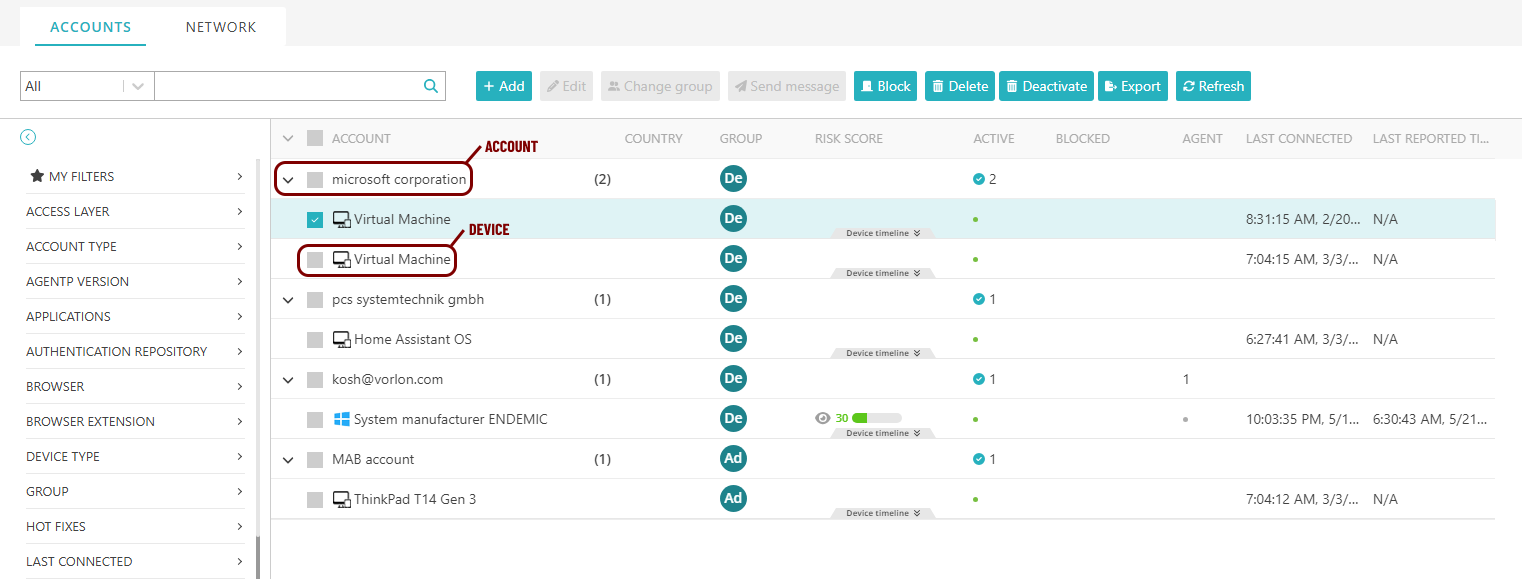
On the Devices screen, in the ACCOUNTS tab, accounts are represented by top-level entries, and devices within these accounts are represented by nested entries, as seen on the example screenshot below.
What are groups in Portnox Cloud?
A group in Portnox Cloud represents a group of accounts that share similar characteristics.
-
You can create groups depending on your needs and company organization. For example, you can create groups for the finance department, the marketing department, and the IT department. Alternatively, you can create groups for network administrators, system administrators, and non-administrative users.
-
You can assign users to groups manually or you can automatically connect groups in Portnox Cloud with groups in external identity management platforms such as Entra ID, Google Workplace, Okta, AD, or LDAP servers.
-
You can define basic access privileges for all members of the group. For example, you can allow the group to access specific Wi-Fi networks, wired networks, and VPNs. Detailed privileges are controlled using policies that you can assign to the group.
-
You can create a maximum of 100 groups.
What are policies in Portnox Cloud?
A policy in Portnox Cloud represents a set of settings, privileges, and requirements, which is assigned to one or more groups. You cannot assign policies directly to accounts.
-
Policies let you configure settings that Portnox Cloud applies to the group in different conditions. For example, you can create a policy that assigns the connected device to a specific VLAN. In a policy, you can also decide what to do when authentication fails, for example, quarantine the device in a special VLAN.
-
You can assign a policy to different groups but each group can only have one policy of each type. You can have multiple access control policies applied to different sites.
Policy types
-
Access control policies
In an access control policy, you decide what the NAS device should do with the user device when the user device succeeds with authentication, fails it, violates a risk policy, or is blocked by the administrator. If successful, the NAS can assign the device to a specific VLAN or ACL. In other cases, the NAS can assign the device to a quarantine VLAN or deny access to the network.
Note:At least one access control policy always exists: the System Default Policy. All groups that are not assigned any other access control policy are automatically assigned this policy.Each access control policy can have maximum 25 rules.
-
Risk assessment policies
In a risk assessment policy, you decide if Portnox Cloud should alert you or if the NAS should deny network access if the risk score of the device is too high. The risk score of the device can be calculated based on different factors such as geolocation, system settings, installed applications, operating system versions, drive encryption, and more.
Note:Portnox Cloud can calculate the risk score only if the device has the Portnox AgentP installed or if you integrate Cloud with an endpoint management solution such as Microsoft Intune.Note:At least one risk assessment policy always exists: the System Default Policy. All groups that are not assigned any other risk assessment policy are automatically assigned this policy.You can create a maximum of 15 risk assessment policies.
-
Remediation policies
In a remediation policy, you decide what actions the Portnox AgentP should automatically take on user devices. For example, you can decide that AgentP should automatically update the antivirus software, turn on the firewall, remove an application, and more.
Note:Portnox Cloud can enforce remediation policies only if the device has the Portnox AgentP installed. -
Custom RADIUS attribute policies
In a custom RADIUS attribute policy, you can define up to 30 custom attributes and later assign them to groups, allowing you to control which custom attributes are sent to which NAS devices when the connecting device is in a specific group. Custom RADIUS attributes are used by many NAS devices to extend the capabilities of RADIUS authentication and authorization. They let you include additional information in RADIUS messages, enabling more granular control over access and policies.
You can create a maximum of 25 custom RADIUS attribute policies with a maximum of 50 attributes per policy, a maximum of 20 mapping rules inside a group mapping, a maximum of 5 levels of nesting in the condition builder query, and a maximum of 30 condition rules in the condition builder query.
-
TACACS+ authorization policies
In a TACACS+ authorization policy, you can decide what members of the group can do when accessing a TACACS+ NAS device. You can define which commands are allowed and which are forbidden, as well as control parameters of the session such as the privilege level, the timeout, and allowed services.
-
Custom SAML attribute policies
In a custom SAML attribute policy, you can decide what custom SAML attributes will be sent to the client by Portnox Zero Trust Network Access (ZTNA) for web-based applications. This is especially useful for integration with resources such as Cisco ASA, where custom SAML attributes can be used to control VPN access rights, for example, to allow only users from a specific group to access a particular web application.
A custom SAML attribute policy contains static values, but you can dynamically apply such policies to groups based on different conditions, such as the device operating system, the specific web application, Entra ID group, and more. For example, you could configure conditions where one set of attributes is sent if the user belongs to the Sales group and uses Salesforce as the application, while a different set of attributes is sent if the user belongs to the Marketing group, and preventing them from accessing Salesforce through the company VPN.
Custom SAML attribute policies can also be used if the web application requires specific (static) SAML attributes, for example, Paylocity. However, custom SAML attribute policies will not work for web applications that require dynamic attributes coming from the identity provider, for example, Grammarly, Bill, Logitech. In such cases, as described in our documentation, you need to configure custom attributes in the identity provider directly, not in Portnox Cloud.
What are sites in Portnox Cloud?
A site in Portnox Cloud represents a physical location, such as an office, where a specific NAS device is located.
-
You can assign NAS devices to sites manually or based on the NAS device IP address.
-
The only setting that is specific to a site is the access control policy.
NAS devices in sites can have one of the following icons:
 – Wired device
– Wired device – Wireless device
– Wireless device – RADIUS/TACACS+ (terminal/shell) direct access
– RADIUS/TACACS+ (terminal/shell) direct access – Other
– Other
