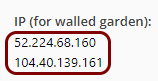Configure a guest Wi-Fi network
In this topic, you will learn how to configure a guest Wi-Fi network in Portnox™ Cloud using a captive portal.
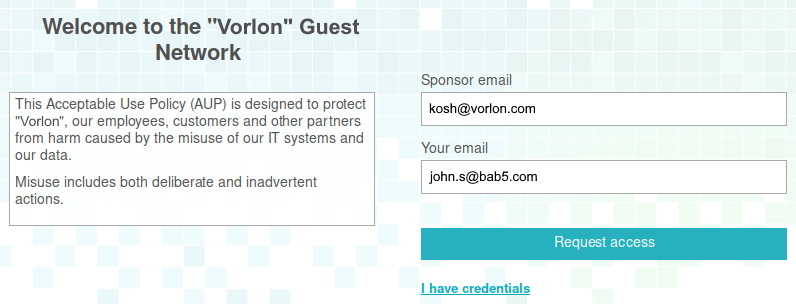
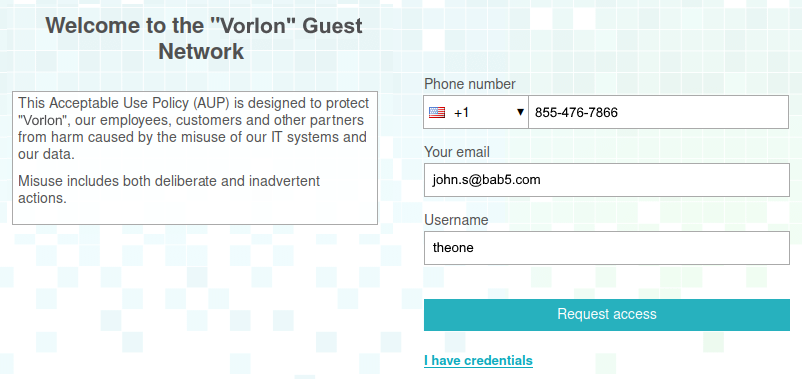
The guest Wi-Fi network is a separate Wi-Fi network with a unique SSID, which lets guests of your organization access the Internet and limited local resources with no connection to the corporate network. When a guest connects to your guest Wi-Fi network using a shared password or no password, they can be redirected to a captive portal. After they complete the steps in the captive portal, the Wi-Fi access point connects them to the Internet and selected local resources.
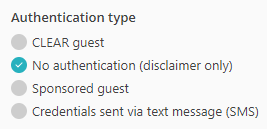
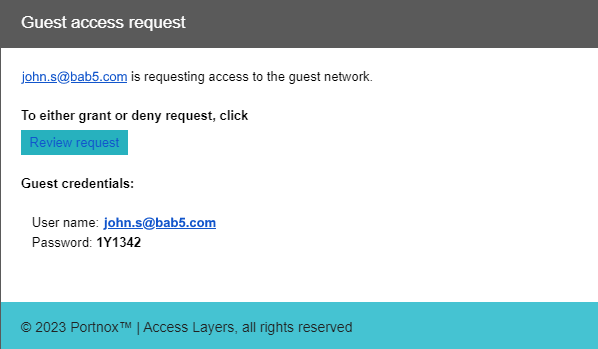
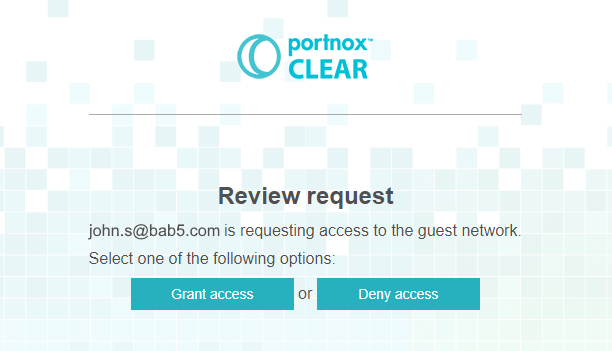
Most Wi-Fi controllers allow you to create a guest network and let you create a simple captive portal managed by the controller. The Portnox Cloud captive portal gives you some unique choices such as the ability for organization employees to authorize guests. This is possible, because it works together with the RADIUS server.
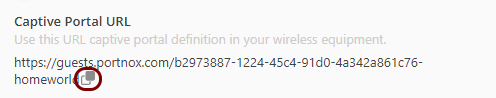
There is no universal standard or protocol for captive portals. The Portnox Cloud captive portal works only with the following network controllers and their internal standards:
- Cisco Meraki
- Cisco
- HPE Aruba
- RUCKUS Networks
- Juniper Mist
- Extreme WiNG
- Aerohive (legacy, now Extreme)
- Fortinet
- Ubiquiti UniFi
- WatchGuard
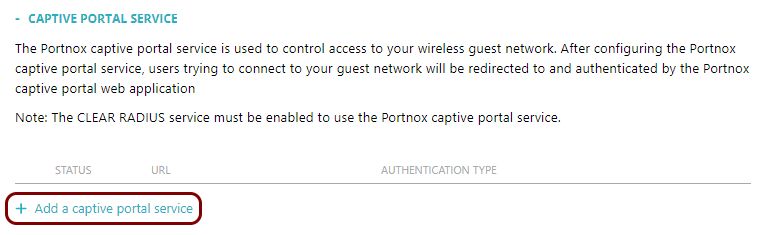
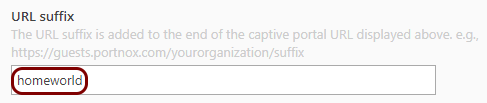
To set up a Portnox Cloud guest Wi-Fi network, follow these steps.
Result: You have added a captive portal service.
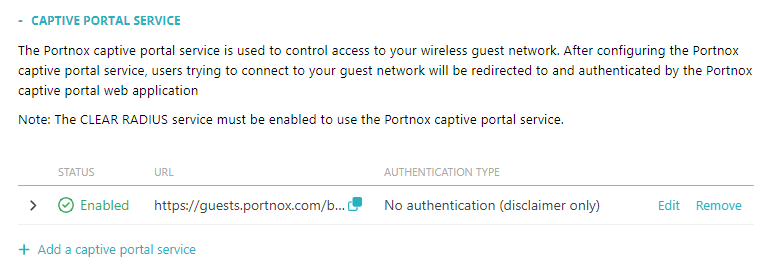
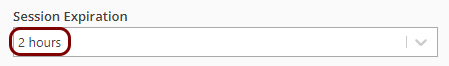
Portnox Cloud counts the number of concurrently connected guests devices. If a device remains connected, the count will be reduced by one on the following day. However, if a guest device gets disconnected, and if the duration of the previous connection has not exceeded the value specified in the Session Expiration property, the next connection from the same device will be allowed without authentication in the Captive Portal. Otherwise, the connection will be counted as a new device, so the count will increase by one.
For specific instructions on setting up guest Wi-Fi access on specific network controllers, see the following topic: Configure wireless devices to work with Portnox Cloud.