Onboard Linux devices with certificates using Certmonger and SCEP
In this topic, you will learn how to obtain Portnox™ Cloud user certificates for managed Linux devices using Certmonger and SCEP.
To connect managed Linux devices to networks managed by Portnox Cloud, you can use a configuration management tool like Ansible, Chef, or Puppet to distribute commands to managed devices. These commands use the Certmonger package to request, download, and monitor user certificates for Cloud and then configure network settings on these devices to use these certificates to connect to the network.
This topic helps you prepare scripts for Ansible, Chef, Puppet, or other configuration management tools by teaching you how to request, download, and monitor device certificates.
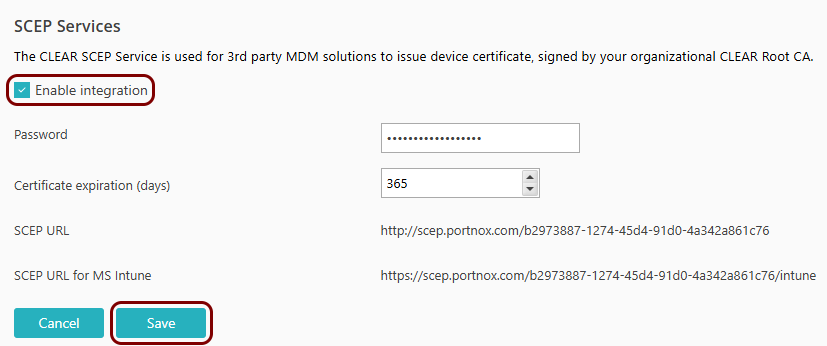
Turn on the Portnox Cloud SCEP services
In this section, you will configure Portnox™ Cloud to provide SCEP services to your devices.
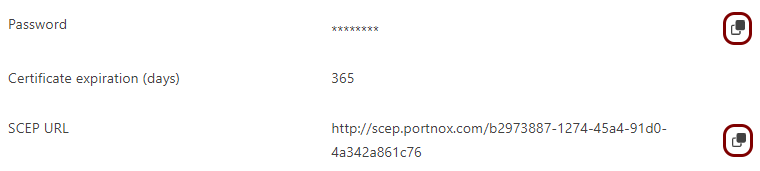
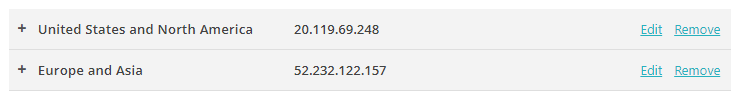
If you have previously turned on the Portnox Cloud SCEP services, skip to the step in which you get the Cloud SCEP URL and secret.
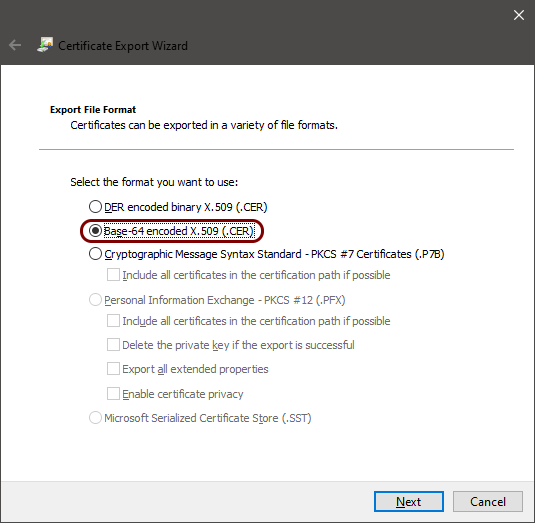
Download and convert the root CA certificate
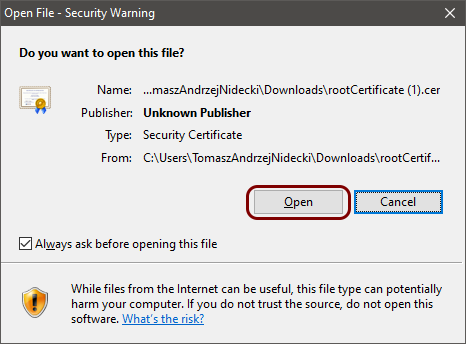
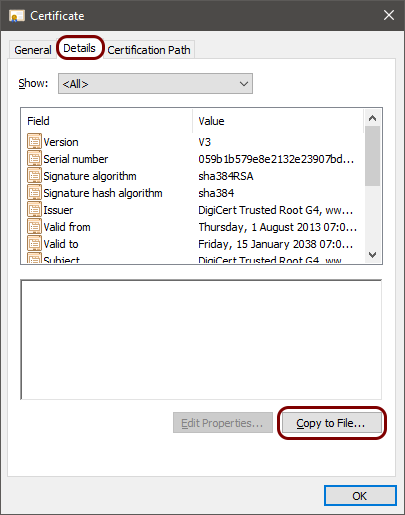
In this section, you will download the Portnox™ Cloud root CA certificate> from the Cloud portal and convert it to a format that you can later use to connect to the network.
Request the device certificate using Certmonger
In this section, you will use the Certmonger software available on all Linux distributions to request a certificate for your device using the SCEP protocol and Portnox™ Cloud SCEP services.
Result: You have obtained a private/public key pair for your device, which you can now use to configure your connections to your networks managed by Portnox Cloud.
Troubleshooting: use $sudo getcert list to list your Certmonger request and see any reasons for potential problems.
Configure your network connection with the Portnox Cloud certificate
In this section, you will configure NetworkManager on Linux to connect to the network managed by Portnox™ Cloud using your user certificate and private key.
Distribute the prepared configuration using configuration management
Refer to the documentation of your selected solution, such as Ansible, Chef, or Puppet, to use the above commands in scripts that are distributed to managed devices.