Onboard a Linux device through self-onboarding
In this topic, you will learn how to onboard using the self-onboarding portal, a Linux machine, and a wired or wireless network managed by Portnox™ Cloud.
Authenticate with the self-onboarding portal
In this section, you will learn how to authenticate with the self-onboarding portal using your corporate identity.
-
Enter the URL of the self-onboarding portal in your browser.
To learn how to set up the self-onboarding portal and obtain the URL, see the following topic: Set up the self-onboarding portal.
-
Click on one of the available buttons representing authentication repositories. Then, complete the authorization
process as required by your authentication repository.
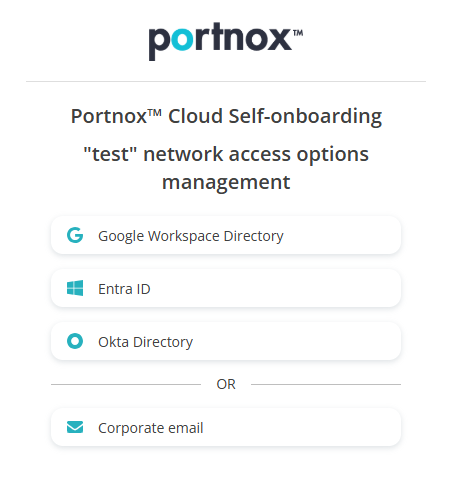 Note:The buttons available on this page will depend on the authentication repositories integrated with your Portnox Cloud. It is very likely that your organization will only use one of them. The Corporate email option is available only if you configured the self-onboarding portal to allow end-users to use and create Portnox accounts using the self-onboarding portal.
Note:The buttons available on this page will depend on the authentication repositories integrated with your Portnox Cloud. It is very likely that your organization will only use one of them. The Corporate email option is available only if you configured the self-onboarding portal to allow end-users to use and create Portnox accounts using the self-onboarding portal.- Optional:
If the Corporate email option is available, and you want to use a Portnox account to
authenticate with the self-onboarding portal, click on the button, enter your email address in the
Email field, and then click on the Sign In button. Then,
check your email account. You will receive a code via email. Copy the code, paste it in the
Activation code field, and click on the Confirm
button.
- Optional:
If the Corporate email option is available, and you want to use a Portnox account to
authenticate with the self-onboarding portal, click on the button, enter your email address in the
Email field, and then click on the Sign In button. Then,
check your email account. You will receive a code via email. Copy the code, paste it in the
Activation code field, and click on the Confirm
button.
- In the Select your device’s operating system field, select the Windows option.
- Continue with the next sections depending on your requirements.
Get and convert the certificate
In this section, you will learn how to get the certificate issued by Portnox Cloud and how to convert it into separate files usable for Linux.
-
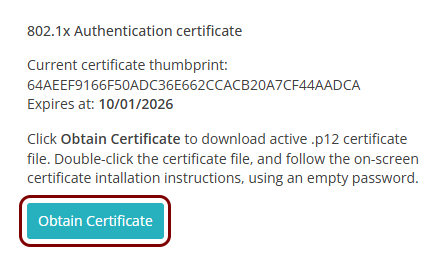
Click on the Obtain Certificate button to download the certificate.
-
Extract your private key to a separate file.
$openssl pkcs12 -nocerts \ -in /path/to/downloaded_file.p12 \ -out /path/to/key_file.pem-
Replace /path/to/downloaded_file with the name and location of the file you downloaded in the previous step.
-
Replace /path/to/key_file with the name and location of the file where you want to save your private key.
-
In the Enter Input Password: prompt, press Enter (empty key).
-
In the Enter PEM pass phrase: prompt, enter the password to use for your private key (you will later use that password when configuring the network).
Example:
$openssl pkcs12 -nocerts \ -in /home/vboxuser/Downloads/vorlon.p12 \ -out /var/portnox/protected.pem -
-
Extract your user certificate to a separate file.
$openssl pkcs12 -nokeys \ -in /path/to/downloaded_file.p12 \ -out /path/to/certificate_file.pem-
Replace /path/to/downloaded_file with the name and location of the file you downloaded in the previous step.
-
Replace /path/to/certificate_file with the name and location of the file where you want to save your user certificate.
-
In the Enter Input Password: prompt, press Enter (empty key).
Example:
$openssl pkcs12 -nocerts \ -in /home/vboxuser/Downloads/vorlon.p12 \ -out /var/portnox/public.crt -
Download and convert the root CA certificate
In this section, you will download the Portnox™ Cloud root CA certificate> from the Cloud portal and convert it to a format that you can later use to connect to the network.
- Open the Portnox Cloud portal and log in.
-
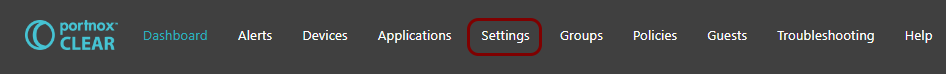
In the Cloud portal top menu, click on the Settings option.
-
In the Cloud portal left-hand side menu, click on the Services > CLOUD RADIUS SERVICE > Cloud RADIUS instance option.
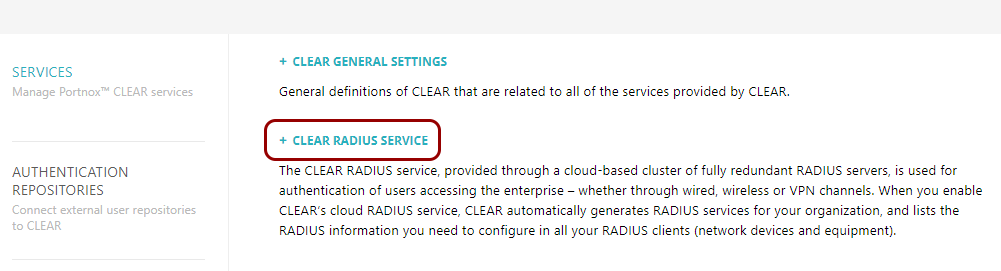
The right-hand pane shows the list of active servers.
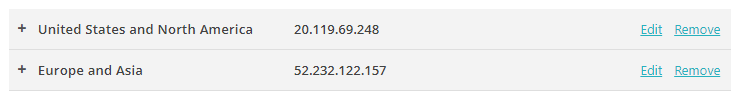
- Click on any of the active RADIUS services to show its configuration.
- Click on the Download root certificate link to download the root CA certificate.
-
If you’re working on a Linux desktop, use OpenSSL to convert the certificate to PEM format.
$openssl x509 -inform der \ -in downloaded_file.cer \ -out certificate.crtNote:The file extension does not identify the certificate format. PEM format certificates most commonly use the .crt extension, but in some operating systems, they may use the .pem extension. On the other hand, the .crt extension may also be used by DER format certificates. Read more about certificate formats and file extensions in the following topic: Certificate formats.Then, skip to the next section.
For example:
$openssl x509 -inform der \ -in rootCertificate.cer \ -out /var/portnox/portnox_ca.crtNote:The remaining steps in this section are for Windows desktops only. -
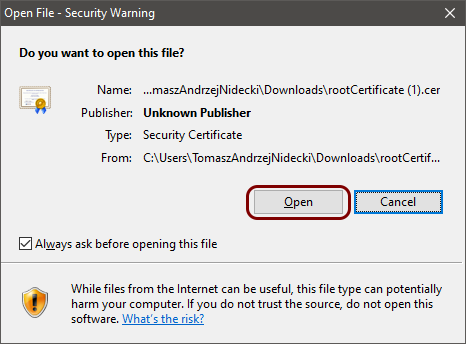
If you’re working on a Windows desktop, double-click on the downloaded certificate file and click on the
Open button in the Security warning window.
-
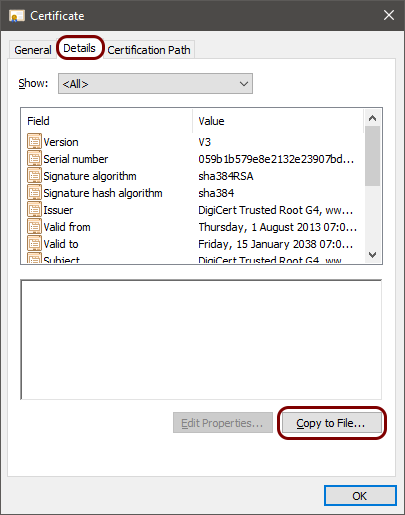
In the Certificate window, click on the Details tab and then click on
the Copy to File button.
-
In the Certificate Export Wizard, export the certificate in base-64 encoded format.
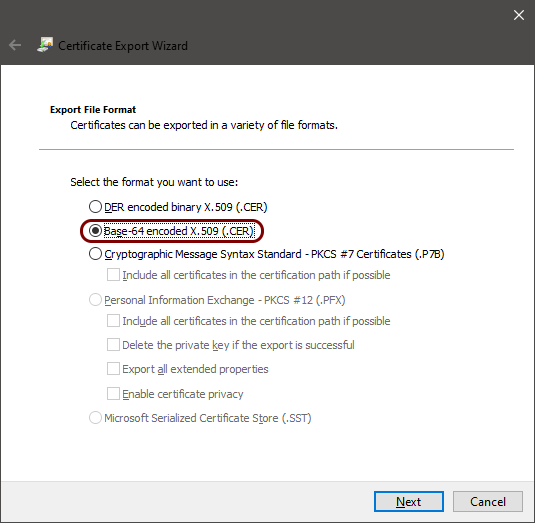
- In the first step of the wizard, click on the Next button.
- In the second step of the wizard, select the Base-64 encoded X.509 (.CER) option.
- In the third step of the wizard, select a file to save the exported certificate, and click on the Next button.
- In the last step of the wizard, click on the Finish button. Then, close the Certificate window.
-
Copy the exported certificate to the Linux device.
The exported base-64 encoded file is a simple text file. If you’re running Linux in a virtual machine, you can simply copy and paste the content of the file into a relevant file in Linux.
For example, save the file as /var/portnox/portnox_ca.crt.
Configure your network connection with the Portnox Cloud certificate
In this section, you will configure NetworkManager on Linux to connect to the network managed by Portnox™ Cloud using your user certificate and private key.
-
Edit the NetworkManager connection file for the network to connect to.
Examples:
-
$sudo nano \ '/etc/NetworkManager/system-connections/'Wired connection 1.nmconnection' -
$sudo nano \ /etc/NetworkManager/system-connections/HOMEWORLDWIFI1.nmconnection
-
-
Add the following section to the configuration file:
[802-1x] ca-cert=/path/to/radius_ca_file.crt client-cert=/path/to/public_key.crt eap=tls; identity=clear@identity private-key=/path/to/protected_private_key.pem private-key-password=private_key_passwordAdditionally, for Wi-Fi connections:[wifi-security] key-mgmt=wpa-eap- Replace /path/to/radius_ca_file.crt with the name and location of the root CA certificate file exported in the previous step.
- Replace /path/to/public_key.crt with the name and location of the file where you stored the user certificate for your device.
- Replace clear@identity with the corporate email address of the user to authenticate.
- Replace /path/to/protected_private_key.pem with the name and location of the file where you stored the password-protected private key.
- Replace private_key_password with the private key password that you set earlier.
Example:
[wifi-security] key-mgmt=wpa-eap [802-1x] ca-cert=/var/portnox/portnox_ca.crt client-cert=/var/portnox/public.crt eap=tls; identity=kosh@vorlon.com private-key=/var/portnox/protected.crt private-key-password=ZSGWhozKJyQRZ9Are6mUeWhXYou9FMbtT -
Restart NetworkManager.
$sudo systemctl restart NetworkManager -
Connect to the network using NetworkManager CLI.
Examples:
-
$sudo nmcli connection up 'Wired connection 1' -
$sudo nmcli connection up HOMEWORLDWIFI1
-
