Integrate Splunk Cloud with Zero Trust Network Access
In this topic, you will find general instructions on how to integrate Splunk Cloud with Portnox™ Zero Trust Network Access.
Create a Portnox Cloud application configuration
In this step, you will create a configuration in Portnox Cloud that will contain all the information necessary to integrate with Splunk Cloud.
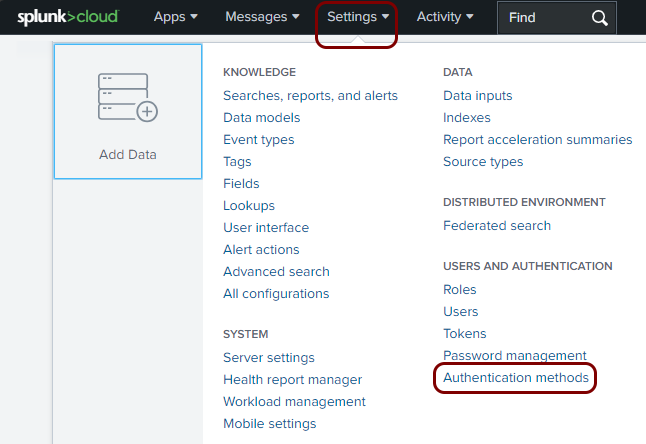
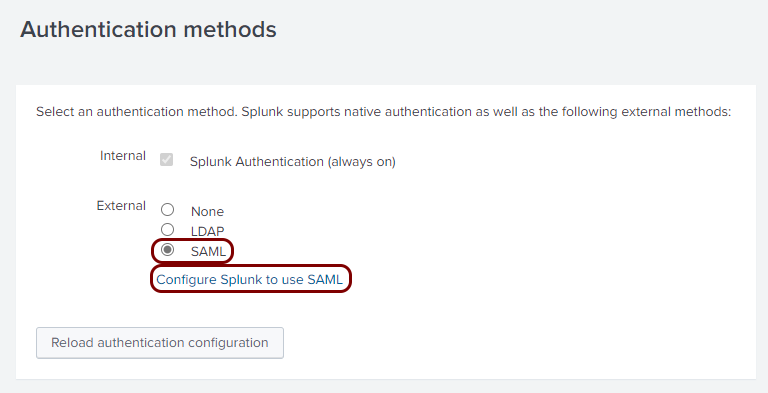
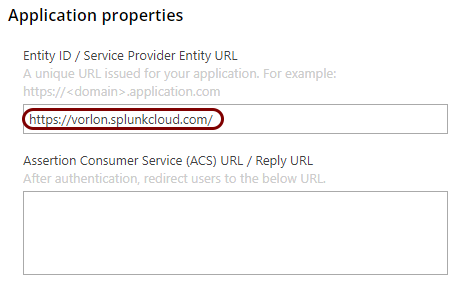
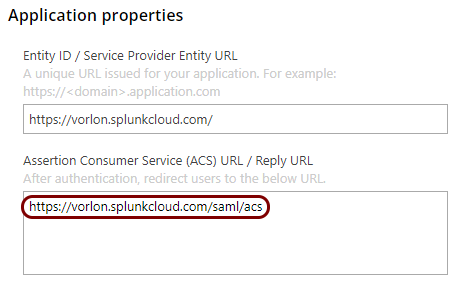
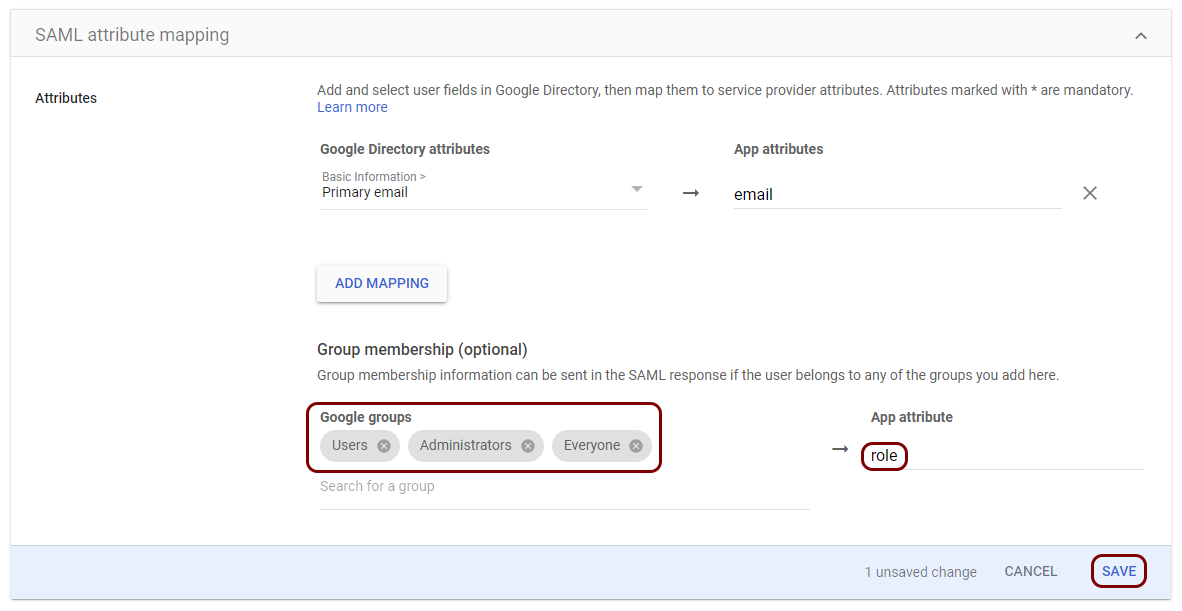
Open your Splunk Cloud SAML configuration
In this section, you will access your Splunk Cloud administrative interface and find the SAML configuration page.
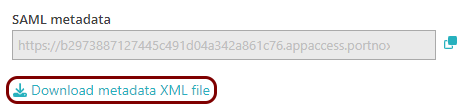
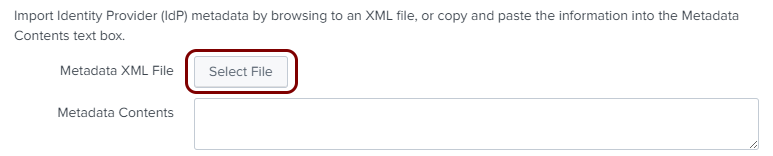
Export metadata from the Portnox tab and upload it in the Splunk tab
In this section, you will export the metadata from Portnox Cloud into a file and upload that file in the Splunk Cloud SAML configuration section.
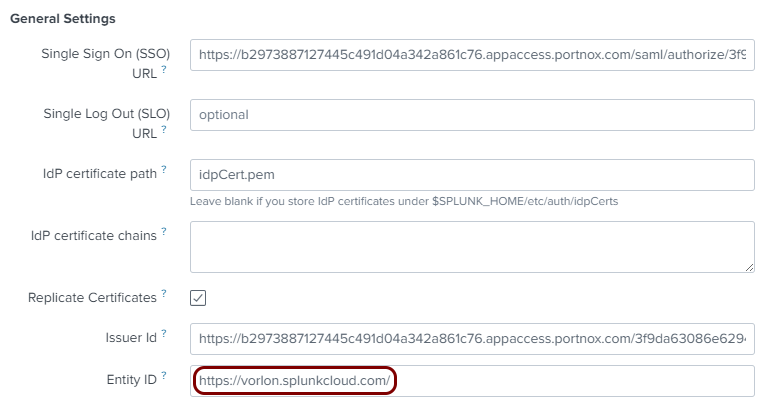
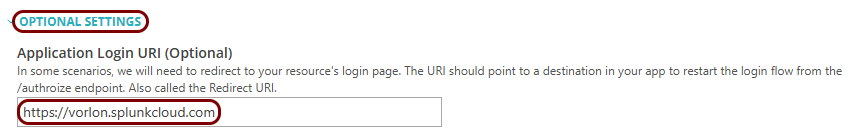
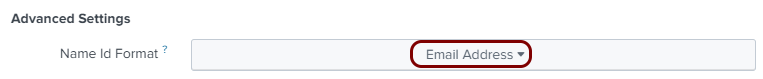
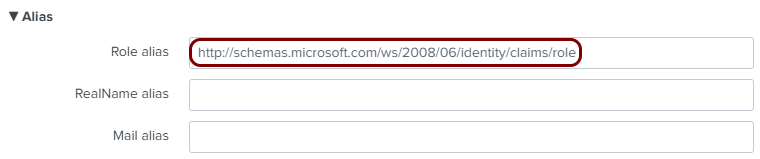
Enter configuration values in the Portnox tab
In this section, you will enter configuration values in the relevant fields in Portnox Cloud.
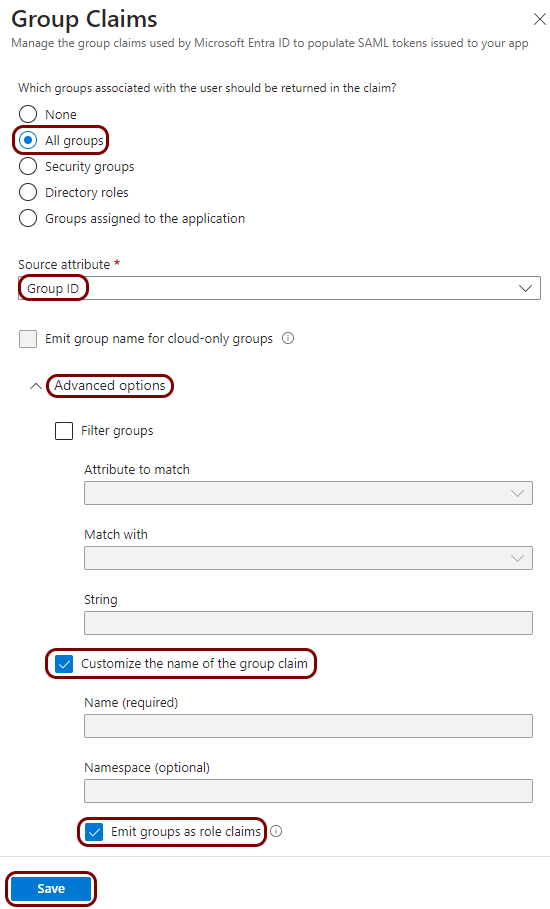
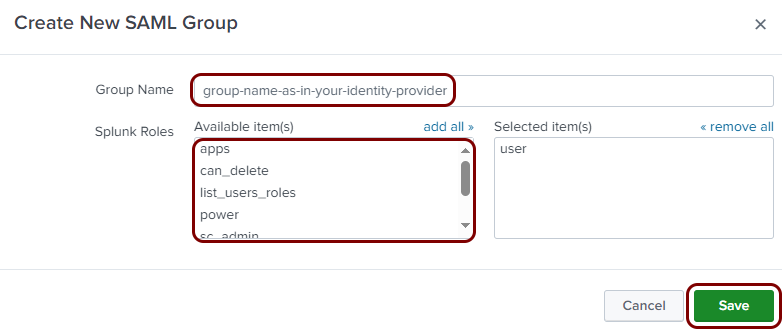
Finalize the configuration
In this section, you will finalize the configuration in Portnox Cloud and Splunk Cloud.
Result: You have configured Splunk Cloud to be accessible using Portnox Zero Trust Network Access.